Every day, millions of accounts are protected by passwords, making them prime targets for cyberattacks. One crucial technique used to enhance password security is salting.
But what exactly is salting, and how does it work? How are passwords actually kept safe from hackers? And does salting keep your passwords safe? Let’s find out!
Table of Contents
What is Password Salting?
Password salting is a technique to protect passwords stored in databases by adding a string of 32 or more characters and then hashing them. Salting prevents hackers who breach an enterprise environment from reverse-engineering passwords and stealing them from the database.
Password salting increases password complexity, making them unique and secure without affecting user experience. It also helps prevent hash table attacks and slows down brute-force and dictionary attacks.
Password security is a vital part of cybersecurity. Passwords are used everywhere. When you log into an account, you enter a password, used to verify your identity.
What is Salting?
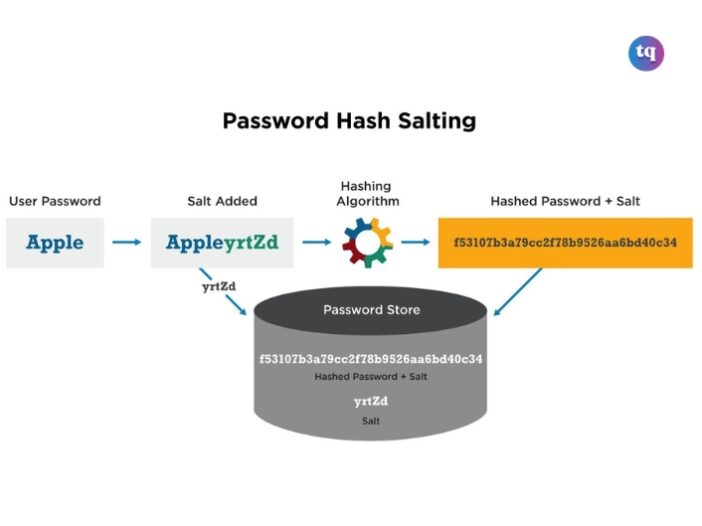
Salting is the process of adding unique random strings of characters to passwords in a database or each password before the password is hashed. This is done to change the hash and make passwords more secure.
The string of characters added to the password is called the salt. A salt can be added in front or behind a password. The salt is not made public and is known only to the site.
How Does Salting Work?
When you create a website or app account, the password you use has to be stored, so you can be verified the next time you visit the site.
But this password cannot be stored as plaintext i.e. without any form of formatting or coding. The password has to be hashed to prevent hackers from easily accessing your account.
Say you sign in to a site with this password: myPassword. Before that password gets hashed, a salt value is added to it. If the salt value for that particular site or user is MUOrocks%, your salted password becomes myPasswordMUOrocks%.
The salted password is then hashed and stored in the database alongside other password hashes.
What Is the Difference Between Encryption, Hashing, and Salting?
Salting, hashing, and encryption are security techniques used every day across sites and systems. They are cryptography terms necessary for password security. But how do they differ?
Encryption
Encryption is a form of cryptography where information is encoded mathematically and can only be accessed and decoded by a person with an authorized key.
The information that needs to be secured is translated from plaintext to ciphertext using an algorithm that makes the information undecipherable to unauthorized users.
Encryption is a two-way process, which means that encrypted data can be reversed and read, but only by those with the right decryption key.
Hashing
Hashing is the process of transforming information that you want to be kept secure into a string of characters also known as the hash. It’s basically scrambling information using an algorithm.
Hashing is a one-way cryptographic function and this means that, unlike encryption, it cannot generally be reversed. The only way you can decipher a hash is by comparing it with another hash with a known plaintext value.
Hashing is used to validate your authenticity. When you log into a website and type in your password, the hash of your password is compared to the hash identified with your account. If the two hashes are the same, you are granted access to the site.
Salting
Salting is another layer of security added to hashing. To make a hash more secure, unique strings of characters are added to the password before hashing to change the hash altogether.
Why Are Passwords Salted?
Salting is very important in security. It helps reduce the risk of malicious hackers getting the passwords.
Simply storing passwords in databases is a very insecure method of keeping users privacy. Any skilled hacker could get into the database and have access to all the accounts on the site.
Let’s see why you should salt your passwords.
1. To Strengthen Weak Passwords
Salting adds another level of security to the site. When a salt value is added to a password, the hash is changed completely. This makes it very hard to reverse engineer the password and renders the rainbow table useless. Here’s an example.
| Password text | Hash | |
| Original Password | myPassword | deb1536f480475f7d593219aa1afd74c |
| Salted password | myPasswordMUOrocks% | 51ae8ec80ae589f4270a1260841650a1 |
As you can see in the table, the hashes are completely different. The password remains the same when you visit the site, but the hash is more secure against exploitation. Salting is especially important when users use weak and popular passwords like “password” or “12345”. Salting lowers the risk that comes from weak passwords.
2. To Make Password Hashes Unique
Salting is also important when two or more users have the same passwords. Adding different randomized salts to each password helps to make each unique. For example, if your password is iL0veCh3ese! and another user, Chioma, has that exact password, salting is used to make those password hashes unique.
| Password | Salt Value | Salted Password | MD5 Hash | |
| You | iL0veCh3ese! | Am4la! | iL0veCh3ese!Am4la! | 31fda55ee57bc4c49ef6e0c99b0ba904 |
| Chioma | iL0veCh3ese! | ew3du? | iL0veCh3ese!ew3du? | cf0bea59647ba39e058a20c14fc10b0d |
Now these passwords, although the same, have completely different hashes. When you look at the hashes, you will never be able to recognize that the two users share a password.
Choosing a Good Salt
Choosing a good salt is as important as choosing a password. A good salt should be unique. Ensure you use unique characters and/or symbols that would make your hash more secure.
The salt you choose for your website shouldn’t be predictable or easily guessed, like the name of the site or user. Another added plus is using long salts.
The best way to choose a unique and strong salt is to use salt-value generators. These help you create random and strong salts to increase your security.
Do not store salts along with the password database, and do not use the same salts for all passwords. Another good salting tip is to change the salt every time a user changes their password.
Is Salting Effective in Boosting Security?
Yes. Salting does increase the security of a password. When you salt a password, it is impossible for a hacker to crack a password using dictionary tables or rainbow tables.
Brute forcing the hashed password is also futile because it would take a very long time before the perfect combination of the hash is found. This way, passwords are more secure and safer from hackers.
Password Salting and Password Peppering: What’s the Difference?
Let’s first know what password peppering is – a pepper is a random value that is added to a password before it is hashed.
Although password salting and password peppering are similar techniques to add more characters to passwords before hashing them, the following are the major differences between both:
- Salt is stored in the database in plain text, while in peppering, pepper value (random characters added to passwords when users create accounts) is not stored in the database.
- When the user logs in, the salt is added to the password > converted to a hash > hashed value is verified to complete the login. While in peppering, the application has to run each combination of pepper value and password until the generated hash is verified against the one stored in the database.
Peppering makes password hashes more secure when compared to password salting. Even if attackers gain access to a password database, they will need to run hundreds of more iterations to decode a password hashed with random pepper compared to a password hashed with salt value.
Which Attacks Can Password Salting Prevent or Minimize?
Attackers use many tools to crack password hashes. This is because hash tables are designed to be fast but are not necessarily secure. By adding randomness to the original plaintext password value before hashing, salting ensures that a different hashed value is generated.
1. Brute-force attacks
In this type of attack, hackers try to guess every possible password combination and then run these combinations through a hashing algorithm. Once a match is found, they can find the original password. Since password salting creates unique hashes for each password, the attacker cannot guess the original password by brute force.
2. Dictionary attacks
Dictionary attacks are the advanced version of brute-force attacks. In this type of attack, bad actors try the most common password word and character combinations. They use a prearranged word list with their computed hash and then compare the hashes from a stolen password table with every hash on the list.
If they manage to find a match, they can easily find the password. Salting makes this process more difficult and mitigates dictionary attacks.
3. Rainbow table attacks
Attackers often use rainbow tables to crack unsalted hashes. A rainbow table is a pre-computed database of decrypted hash passwords, which attackers can search to find the desired hash.
But, when salting is used for each password, attackers will fail. Even if they knew the salt, they would still need to build a rainbow table for each salt. This is how password salting helps prevent rainbow table attacks.
Tips for Making the Best Use of Password Salting
Here are some ways to make the best use of password salting to strengthen security and prevent password attacks:
- Create a unique salt for every user and password. A unique salt for every user and password increases the computational power required by an attacker to crack passwords. A unique salt should also be generated every time users change their password.
- Store salt and password separately. Storing the salt separately from the password makes it harder for attackers to reverse-engineer the password.
- Make the salt at least the same length as the output hash. The length of the salt value should be long and at least of the same length as the output hash.
- Use a pseudo-random number generator. Using a cryptographically secure pseudo-random number generator to salt the values of hash passwords generates random and unpredictable values that are difficult for attackers to compromise.
- Add a secret key to the hash. This ensures that the password can only be validated if the secret key is known. Storing the key separately on an external system also stops hackers because they need to access both internal and external systems to carry out a password-based attack.
- Don’t use usernames as hash values. Usernames are predictable and often reused, leaving the account susceptible to hacking.
- Don’t use a systemwide salt. A systemwide salt allows an attacker to use hash tables to steal passwords and compromise accounts. Instead, each password created for a user should be hashed and salted separately.
Conclusion
Salting is a powerful technique that significantly enhances password security by adding uniqueness to each password hash.
While it is not a standalone solution, when combined with other security measures, it provides a robust defense against cyberattacks.
By understanding and implementing effective salting practices, you can protect your data and maintain secure systems.